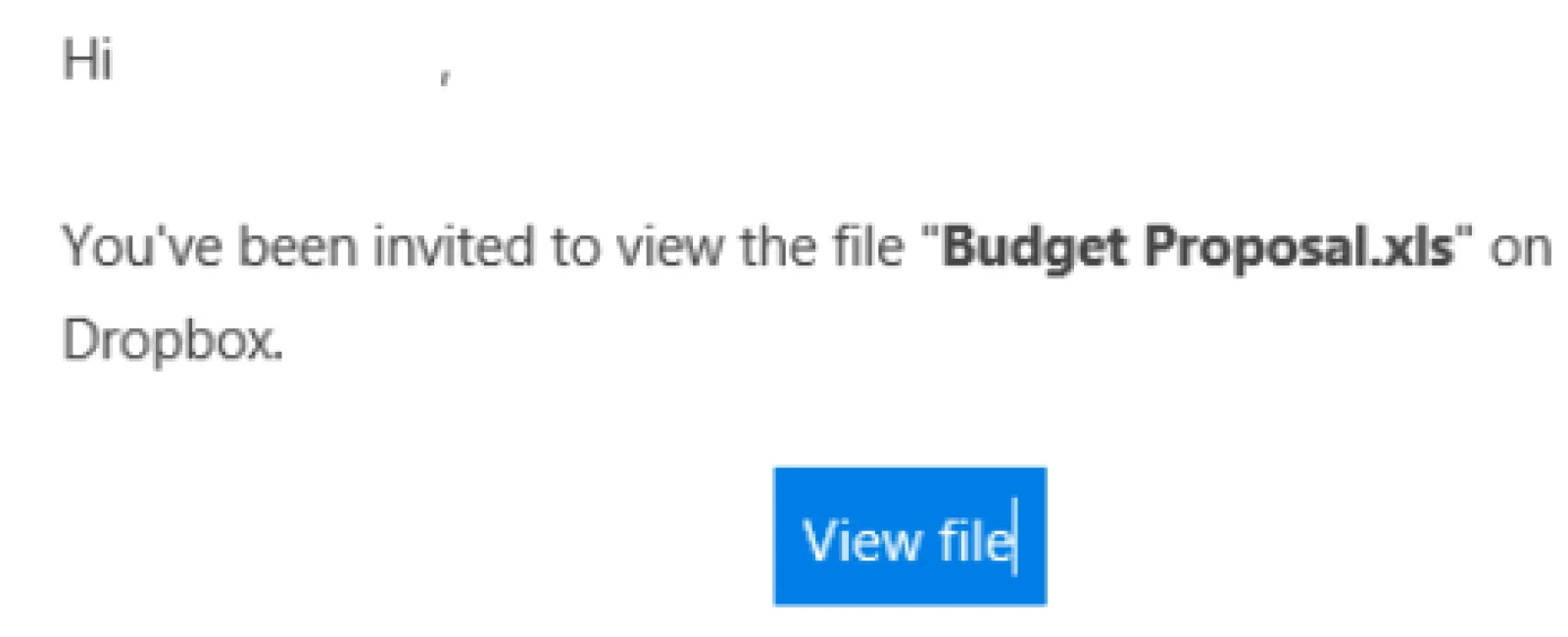
Phishing is a term that describes emails that look legitimate but are actually designed to fool users into revealing personal information such as passwords, bank account numbers, etc. Phishing (the act of sending emails to illicitly collect personal information) has been around for many years. However, we have seen a surge in the volume hitting small business lately. These emails come in many forms and are specifically designed to fool you and your staff. A common one is shown below and it tends to fool a great many users.
This is just one example of many schemes going on right now. If a user clicks on the link in the email it takes them to a website that asks them to verify themselves by typing in their Office 365, Gmail or Yahoo credentials. That’s where the criminal strikes gold. With those credentials he immediately has access to all of the data in the related account. Typically the criminal (via the use of automated bots) reads the contact list of the victim and sends out the same email to everyone. The process repeats itself and spreads like wildfire from one contact list to another. The aftermath of damage control can be both time intensive and expensive depending on what damage was done and what data may have been compromised.
In nearly every case, the emails are detectable as phishing but the user must be both wary and educated on how to detect them. Tell-tale signs usually are there but you have to know where to look. A busy employee may not take the time to inspect emails fully or understand the importance of doing so. This is where security training is vital. Check with us if you are interested in a training program for your staff. A little precaution can go a long way.
You may wonder why these emails are not simply filtered out by anti-spam or anti-virus software. There are many reasons for this. Primarily it is because there is nothing in the email itself that is malicious. There is no virus, code injection, attachment or other threat present in most cases. It is simply a url to a website that on average only is active for 24 hours. By the time it is flagged as a potential threat the criminal has moved on. It is nearly impossible to stop these types of phishing emails at the moment so learn to recognize them and be wary of everything no matter how legitimate it may appear.
Today’s blog author is Mike Farlow, CEO of ComTech